Security & Privacy for the Internet of Things (IoT)

1. Introduction
Computers have become smaller and more powerful than they used to be in the 1950s. This has allowed us to provide computing power to any object we desire! The technology that allows us to connect a plethora of everyday objects to the internet and letting them communicate with each other and with service providers to improve the quality of life for humans is known as the Internet of Things (IoT). IoT is taking over the world at a rapid rate and this is majorly due to the various applications that this technology provides, it ranges from smart homes to smart medical devices to even intelligent transportation.
Even though IoT is one of the best technological innovations of the century, there are serious concerns regarding the security and privacy of this technology. Most of the IoT devices that are being pushed out to the market have little to no security measures in place and this poses a huge risk for the consumers as their privacy is questioned and it often leaves them vulnerable to various kinds of cybersecurity attacks. Imagine a situation wherein your smart home (with several IoT devices connected everywhere) were to leak all the data it was collecting about you and your family. This data would be ranging from simple user details to data that depicts behavioural patterns of the occupants in the house. This is extremely sensitive data that puts everyone in your family at risk.
No computer or network is ever fully secure but if strong security measures are not taken, it could easily put people at risk. IoT is no exception, the devices provide a lot of value to mankind but if not protected well we can be sure that these devices will become an easy target for attackers. This post is intended to discuss some of the security and privacy challenges in IoT, known cyber-attacks and a few pointers towards how manufacturers and developers can tighten the security of their devices.
2. Security & Privacy challenges in IoT
2.1. The multitude of devices
A lot of people these days are adopting IoT devices to make life a little better for themselves and their loved ones. However, something that they all overlook is with every IoT device they add to their usage, a new attack possibility opens up. Also, there is no fixed firmware that is used in all IoT devices, it’s just a mix of various firmware. So even if a vulnerability is detected, patching all the different firmware and devices is just very hard [1]. Another humongous problem with IoT devices is that every device manufacturer is trying to outdo their competition in pushing devices with novel features as quick as possible to the market, the issue with that is everyone is collectively ignoring the security aspect of the device [2] and instead they just concentrate on new and exciting features!
2.2. Nature of the ecosystem
The devices are really small and placed everywhere, this makes the devices vulnerable to environmental factors and thus it is almost impossible to detect if a device has gone rogue or not. Another major issue is due to size limitations of these devices, they often do not have a lot of memory or compute performance, this gives most manufacturers/ developers an excuse to use weak encryption strategies. Another common issue found in the IoT ecosystem is that most devices come with pre-configured security settings that usually contain hardcoded credentials, open ports and insecure admin portals [2].
2.3. Multiple layers to think about
IoT devices have vulnerabilities at various levels of the stack, i.e. attacks are possible at the hardware level, software level or at the network level. Software attacks are usually cyberattacks whereas hardware and network-based attacks often tend to be physical attacks on the device itself. Most developers often end up treating IoT devices like traditional computers and concentrate a lot on the software-based protection schemes, thereby ignoring the hardware and network layers [3]. A lot of advancements have been made in the hardware front with novel inventions like the blowing up of an e-fuse inside a SoC (System on a Chip) if some alteration of the bootloader is detected. The common issue is that these hardware-based protection schemes have been developed with passive protection in mind and not in cases where the devices might be attacked from both the hardware and software side. In addition, these hardware-based protection schemes are not well-supported for low power embedded units [3]. On the network level, some common attacks would include Man-in-the-middle attacks and fake access point attacks, both attacks involve the hacker acting as a legitimate source of communication and fooling the IoT device into giving them sensitive details [1]. Once an attacker can compromise an IoT device, it can then be used to further attack other devices in the connected network [3].
2.4. Typical consumer behaviour
There exists a very unique view to security and privacy vulnerabilities present in IoT devices in general and that is when consumers borrow, rent, gift, resell and retire an IoT device. Developers of IoT devices usually do not look into this possibility at all. Users normally would borrow a device, rent their device to someone else, gift a used device to someone, resell their used device or retire a device after using it for some time. In each of these cases, the first user’s personal data and credentials will be stored on the device, and when the device is later given to someone else or retired, this residual data often leads to security breaches [4].
2.5. Lack of user knowledge
The technology is very new, and most adopters of this technology aren’t aware of the various security measures they need to take to prevent breaches of their system. This includes changing the system default credentials, setting up hard-to-guess unique passwords and not permitting the device to collect information it does not require. “Cyber Hygiene” strategies for IoT is important and must be practised by every user, but it is often ignored, and users are usually oblivious to such a thought [5].
3. Exploits on popular IoT devices
3.1. JoyLink
JoyLink is a very popular smart home solution in China and it supports a lot of smart appliances ranging from washing machines to cameras. Work done by Liu et al. shows that these extremely popular smart home solutions are not so secure after all [6]. The devices have a multitude of security issues such as:
Poor WiFi provisioning on the mobile application indicates that the WiFi credentials are directly encoded into a sequence of IP addresses. This allows the attacker to pass WiFi credentials of their own rogue WiFi access point and the device would directly connect to it.
Communication security was very weak on the Joylink device, the authors who conducted the experiment found out that the crypto key management on the device was terrible. The attackers were able to decrypt live traffic, perform device hijacking, perform an out-of-band device control attack and were even able to impersonate the device.
A vulnerability that the authors of the paper found was that the device had an option to update its firmware but the downloaded binary file for the update was never verified on the device. This would allow hackers to maliciously edit the binary file and inject their code. Another issue the authors identified was that there existed a bug in the code which added an extra slash to the URL that was required to be called to successfully download the firmware. Due to the ignorance of the developers to test their code, the device is rendered obsolete and vulnerable to all sorts of attacks as the firmware cannot be updated at all.
A serious privacy issue that was identified with the Joylink device was that during the WiFi provisioning step, the WiFi credentials were being sent to the cloud which is unnecessary and is a serious privacy issue. Even though the credentials are encrypted with AES encryption, the key used is that of the timestamp which is a very popular cryptography mistake a lot of developers make.
3.2. Withings Blood Pressure monitor
A few medical IoT devices were tested for security vulnerabilities by Wood et al. and the Withings Blood Pressure monitor which is known to be a popular product for measuring the blood pressure of the user was reported to have a vulnerability that allowed attackers to access sensitive information about the user. The authors were able to capture information regarding when the user was measuring their blood pressure by monitoring the network traffic. The flaw was introduced mainly due to the bad programming practices that were used by the developers at Withings. Sensitive data was being sent across the network in clear text which made things very easy for an attacker [7].
3.3. Nest Thermostat
The Nest Thermostat device is a popular smart home IoT device that lets users control the temperature in their houses. Arias et al. found multiple security vulnerabilities on the device, here’s a list of the vulnerabilities reported by the team:
On close examination of the circuit board for the device, they were able to find that the
sys_bootpin was exposed and easily accessible. If the pin was pulled high, the device allowed to boot from a peripheral USB device. This allowed the authors to inject malicious code into the device. Furthermore, they found that by pressing the main button for 10 seconds they were able to hard reset the device and when it booted back up, the ROM did not perform any kind of firmware verification. The malicious code is taken and directly run without any restrictions whatsoever.The authors were able to infiltrate the device via SSH and SFTP. After a few modifications to system files, they were able to create a user account for themselves in the system. This made accessing the device very easy for the authors when inside the same network.
The authors then developed a Trojan horse that could connect to a remote server and await commands. The Trojan horse was injected into the device and they connected the device to a test home network wherein there existed other devices such as smartphones and laptops. The Trojan horse enabled the authors to deploy a rogue DHCP server to shape outgoing DNS requests thereby launching a wider attack that included the various other devices that were connected to the network. Going one step further, the authors were even able to make changes to the base kernel, this allowed them to block certain files from being deleted even if official Nest updates were run, thereby keeping their malicious code safely in the device even after official Nest updates.
3.4. Nike+ Fuelband
The Nike+ Fuelband is a Bluetooth enabled personal fitness tracker that allows users to track basic everyday metrics such as calories burned, steps taken and even sleep patterns. Attacks made by Arias et al. shows how vulnerable a personal device such as this is. The documentation states that external input/output to the internal memory are blocked but the Nike+ Fuelband does not use this feature. An attacker can freely modify the contents of the flash as long as they have physical access to the device itself. The authors were even able to inject a modified firmware onto the device with little hassle [3].
3.5. CogniToys Dino
The CogniToys Dino is a highly revered toy that enables a child to communicate with itself via voice commands. Attacks on smart toys such as these are considered as a very serious issue as it targets children who are usually vulnerable to deception. Valente et al. were able to find several security flaws in the Dino, such as weak encryption techniques that allowed for an eavesdropper attack, and an attack where the authors were able to inject their own content for the toy to speak to the child [8]. These attacks allow the attacker to listen to all the audio conversations that were being exchanged via the toy and also inject their own audio content for the toy to speak to the child. These audio injection attacks are very dangerous as the child trusts the toy and probably thinks the toy is talking to them. This allows the attackers to ask the child to open the door of their house, feed lies about the child’s parents or even insult the child’s appearance/ intelligence, hence eroding the child’s self-esteem at an early age.
4. Mitigation methodologies
There are multiple mitigation methodologies that IoT device developers and the users can adapt to. Here are some of the mitigation techniques that could be employed to tackle the challenges and attacks mentioned in the previous sections:
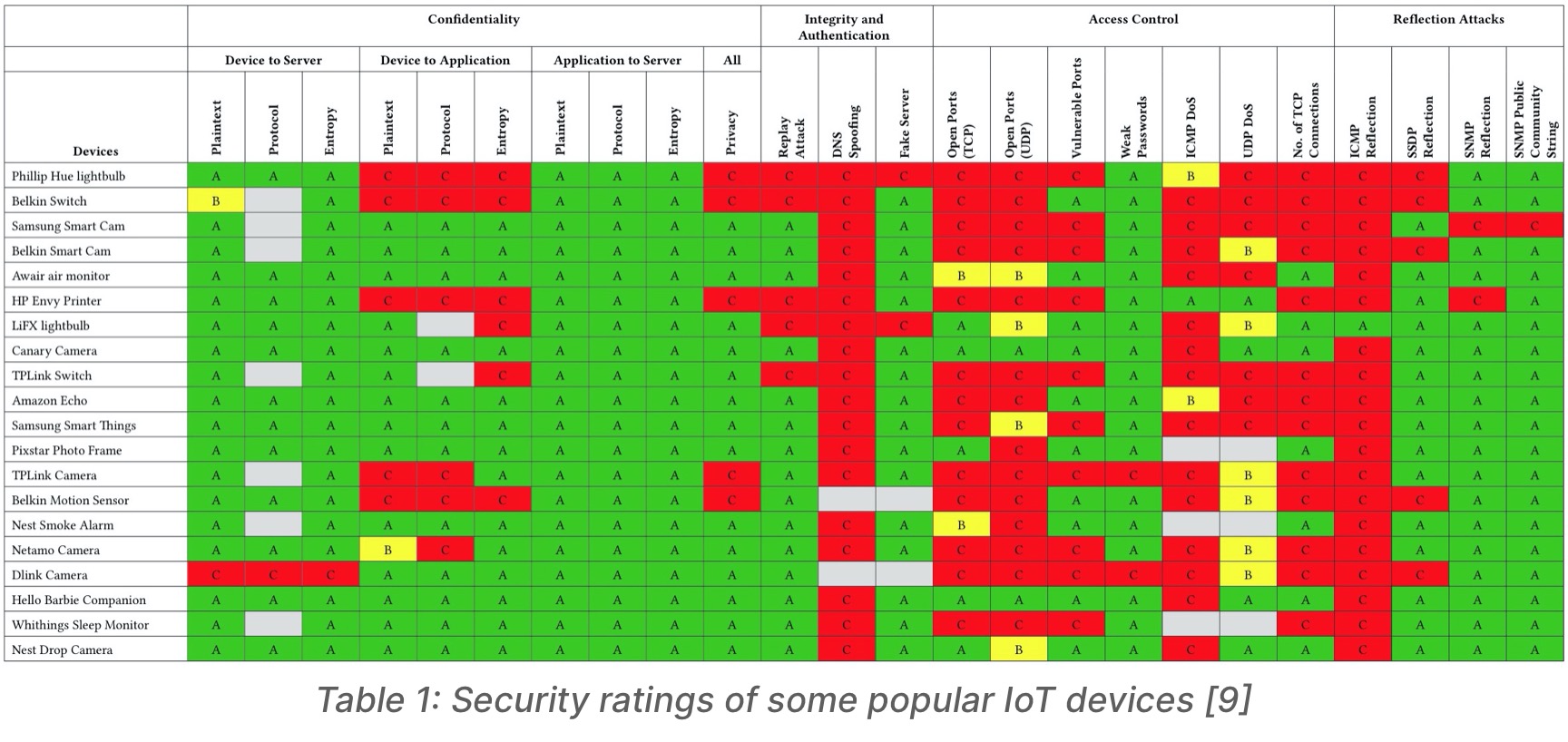
- Loi et al. discuss a novel methodology that uses a level-based rating system for IoT devices in the market. An A-rated system would be considered secure, a B-rated system would be considered moderately secure and a C-rated system would be considered insecure. The threats are categorised along four dimensions – confidentiality of data, the integrity of data, access control of the device and reflective attacks that can be launched from the device. The confidentiality of the system is tested by checking if the system’s encryption protocol is identifiable by simple traffic snooping, if the payload sent by the device on the network contains any plaintext, and checking for the entropy value which usually indicated the strength of the encryption strategies that were used. The integrity of the system is determined through its vulnerability to replay attacks and whether it is vulnerable to DNS spoofing attacks. The access control of the device is determined based on how easy it is for an attacker to gain full access to the device, and also the device is assessed to see how much incoming traffic it can handle before it succumbs to a Denial-of-Service attack. Finally, to check for reflection attacks, the device is sent ICMP messages, SSDP broadcasts, and SNMP request, and if the device responds to any of these protocols then it is deemed as vulnerable to reflection attacks. Table 1 shows the security ratings of various popular devices [9].
Most proven cryptographic algorithms perform exceptionally well on regular computers but not on IoT devices due to their energy, storage and processing limitations. Hence, Ozmen et al. have proposed a set of ingenious cryptographic optimisations that allow developers to use proven cryptography algorithms on small, resource-limited IoT devices. The paper published by Ozmen et al. befittingly titled “Low-Cost Standard Public Key Cryptography Services for Wireless IoT Systems” [10] discusses a specific technique called the Designated Boyko-Peinado-Venkatesan (DBPV) that has low power consumption but uses a small constant-storage overhead to keep up. By having a self-certified ECDH operation, it is possible to remove the overhead introduced by the certificate verification step and when working with DBPV the efficiency gain is improved. The security of BPV as a cryptographic algorithm by itself is well-analysed and it relies on the difficulty in solving the “Hidden Subset Sum” problem [10]. Their experimental analysis has even shown that their proposed methods are up to seven times more energy-efficient over standard cryptographic algorithms. Besides, the authors have made their implementations open-source thereby making their suite of cryptographic optimisations open for all to implement on their own IoT devices.
Since Python is one of the most common programming languages used to program IoT device, Datta et al. have published a paper regarding a very easy-to-use Python library that allows for ILP traffic shaping with minimal effort. The library developed by them is essentially a wrapper for the recv() and send() functions in Python’s existing socket library. The library automatically obfuscates device traffic by packet buffering, payload padding and fragmentation, and randomised cover traffic. The library essentially provides a way for developers of IoT systems a safe way to send information between their devices and cloud services. The use of this library to shape traffic essentially prevents attackers from using the encrypted IoT traffic data and inferring user events, thereby keeping even the encrypted data safe from malicious prying eyes [12].
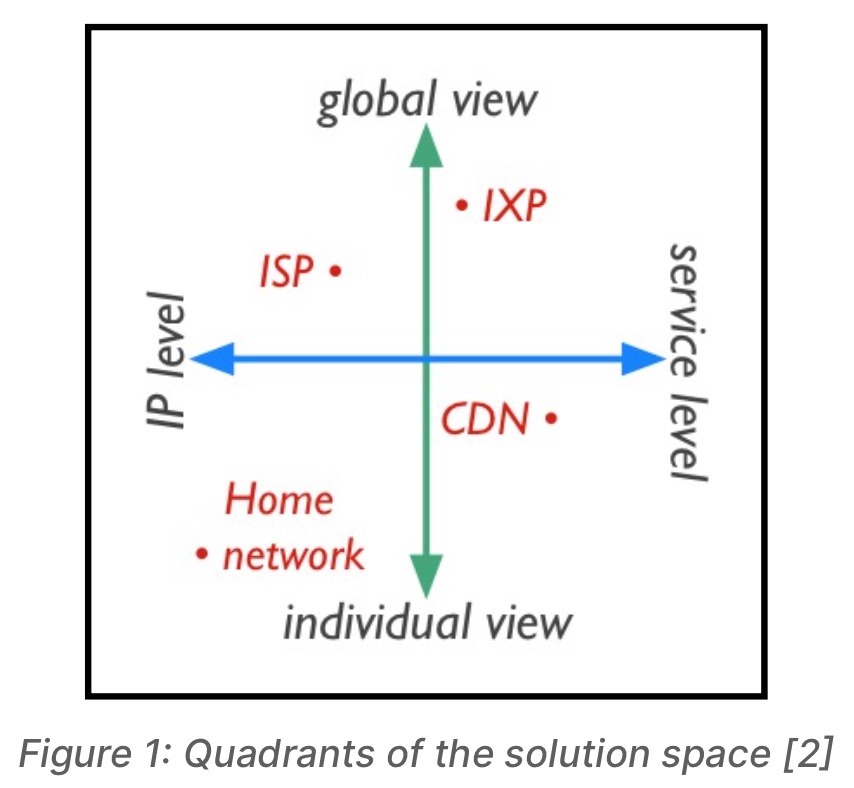
There exist various stakeholders in a fully working IoT system and they would be – device manufacturers, end-users, internet service providers (ISP), internet exchange points (IXP), and content delivery networks (CDN). For a fully secure IoT system, all the various stakeholders must cooperate at their levels. Figure 1 shows the four quadrants of the solution space as described by Benson et al. in the paper “Sounding the Bell for Improving Internet (of Things) Security” [2]. The paper discusses a technique in which monitors are set up at every level of the stack to be able to efficiently mitigate a large scale DDoS attack, to quarantine a node if it is found to have gone rogue, and to detect a botnet during its early stages of growth so as to stop it before it grows into a monstrous DDoS attack. In short, their approach depends on using the internet’s hierarchical topology to our advantage by combining the insights from different deployment locations for detecting and mitigating IoT based attacks.
One of the security and privacy challenges discussed earlier in this post was that of typical consumer behaviour wherein consumers often tend to rent, borrow, gift, resell or retire an IoT device after using it for a while. Khan et al. suggest that developers and manufacturers of IoT devices must plan for the “five communal acts of a consumer” during the design phase. The manufacturers must develop the devices in such a way that they are smart enough to understand these acts of a consumer and adjust themselves accordingly. The re-configuring/ re-login part of the system must be easy to use and the original owner’s data should not be visible to the new owner. When a device is to be retired, the manufacturer’s service running on the device must make sure no residual data of the consumer is left behind and that the device truly is clean, so as to not be vulnerable to exploits by intruders who gain access to the device in the future. The authors also recommend that minimum amount of data regarding the consumer must be stored on the device, so that even in case there is a leakage of data somehow, not all of the critical data regarding the consumer is leaked [4].
Most of the exploits that were discussed in the previous section involved a sketchy procedure to verify firmware updates, this must be looked into seriously by all manufacturers and developers of IoT systems. If the verification is done on the device, then it must be made sure that the onboard verification system cannot be tampered with. An approach to solve this issue by Arias et al. is to only import and run cryptographically signed binaries, so if the signature verification fails then we can be sure that the binaries have been tampered with and thus the firmware will not be run, in addition to notifying the user of possible tampering. Another enhancement suggested by the authors of the paper is that in microcontroller-based IoT devices it is necessary to disable any external ports or debug interfaces to make sure an attacker cannot use those as an easy path to infiltrate the device [3].
Simple changes like using HyperText Transfer Protocol Secure (HTTPS) over HyperText Transfer Protocol (HTTP) to make requests and Secure Real-time Transport Protocol (SRTP) over Real-time Transport Protocol (RTP) can greatly improve the overall security of the IoT system. These changes require very minimal work but provide improved authentication, integrity checking, and safeguards the network against replay attacks when compared to their nonsecure versions [8].
Experts in the field of Information Technology are usually more aware than the general public when it comes to security and privacy issues regarding IoT devices, hence bringing awareness to the common man about the kind of data they expose to all their IoT devices will automatically make them learn and implement “cyber-hygiene” practices to remain safe [5]. Most security attacks can be averted if the everyday user was aware of these issues and used some common sense to safeguard themselves. Some of the simple steps that the consumers can take to prevent themselves from security vulnerabilities are:
Changing system default passwords and security keys to something more unique and harder to crack [2].
Whatever the interface they use, ranging from browser to an application, consumers should spend some time going through all the various settings available to them, and they should change all the system default values to something more unique and switch on all the preferences and options that enable the system to operate more securely [2], [11].
Reconfiguring the router’s DHCP to dish out IP addresses in the 1/16 subnet in itself can avert many attacks as most hackers assume regular users to not have changed these settings on their router [11].
Using privacy-focused browsers and browser plugins can also help with preventing a lot of web-based attacks [11].
5. Conclusion
IoT is such a booming space right now and all the excellent features they provide to help ease the lives of human beings makes the technology very lucrative to consumers. The technology is advancing at a very rapid pace and the manufacturers rarely invest time and energy to look into the security and privacy issues that come bundled with it. Security and privacy have become an afterthought for developers of IoT devices and this must change as a lot of critical user data is on the line with such integral devices. A lot of the common challenges with this technology were discussed, a few of the exploits on popular IoT devices were explored, and some mitigation steps were suggested in this post. This would allow the readers to gain an understanding of the seriousness of this issue and even make them aware of the kind of exploits that are possible on IoT devices. In conclusion, it is known that security and privacy have taken a back seat in most development processes of these devices and that awareness of these issues is not very prevalent, and hence a lot of mitigation and prevention steps need to be taken in this area to ensure the safe adoption and use of IoT devices by consumers.
6. References
[1] J. P. Nzabahimana, “Analysis of security and privacy challenges in internet of things,” in 2018 IEEE 9th International Conference on Dependable Systems, Services and Technologies (DESSERT), pp. 175– 178, May 2018.
[2] T. Benson and B. Chandrasekaran, “Sounding the bell for improving internet (of things) security,” in Proceedings of the 2017 Workshop on Internet of Things Security and Privacy, IoTS&P ’17, (New York, NY, USA), p. 77–82, Association for Computing Machinery, 2017.
[3] O. Arias, J. Wurm, K. Hoang, and Y. Jin, “Privacy and security in internet of things and wearable devices,” IEEE Transactions on Multi- Scale Computing Systems, vol. 1, pp. 99–109, April 2015.
[4] W. Z. Khan, M. Y. Aalsalem, and M. K. Khan, “Five acts of consumer behavior: A potential security and privacy threat to internet of things,” in 2018 IEEE International Conference on Consumer Electronics (ICCE), pp. 1–3, Jan 2018.
[5] J. A. Oravec, “Emerging “cyber hygiene” practices for the internet of things (iot): Professional issues in consulting clients and educating users on iot privacy and security,” in 2017 IEEE International Professional Communication Conference (ProComm), pp. 1–5, July 2017.
[6] H. Liu, C. Li, X. Jin, J. Li, Y. Zhang, and D. Gu, “Smart solution, poor protection: An empirical study of security and privacy issues in developing and deploying smart home devices,” in Proceedings of the 2017 Workshop on Internet of Things Security and Privacy, IoTS&P ’17, (New York, NY, USA), p. 13–18, Association for Computing Machinery, 2017.
[7] D. Wood, N. Apthorpe, and N. Feamster, “Cleartext data transmissions in consumer iot medical devices,” in Proceedings of the 2017 Workshop on Internet of Things Security and Privacy, IoTS&P ’17, (New York, NY, USA), p. 7–12, Association for Computing Machinery, 2017.
[8] J. Valente and A. A. Cardenas, “Security & privacy in smart toys,” in Proceedings of the 2017 Workshop on Internet of Things Security and Privacy, IoTS&P ’17, (New York, NY, USA), p. 19–24, Association for Computing Machinery, 2017.
[9] F. Loi, A. Sivanathan, H. H. Gharakheili, A. Radford, and V. Sivara- man, “Systematically evaluating security and privacy for consumer iot devices,” in Proceedings of the 2017 Workshop on Internet of Things Security and Privacy, IoTS&P ’17, (New York, NY, USA), p. 1–6, Association for Computing Machinery, 2017.
[10] M. O. Ozmen and A. A. Yavuz, “Low-cost standard public key cryp- tography services for wireless iot systems,” in Proceedings of the 2017 Workshop on Internet of Things Security and Privacy, IoTS&P ’17, (New York, NY, USA), p. 65–70, Association for Computing Machinery, 2017.
[11] G. Acar, D. Y. Huang, F. Li, A. Narayanan, and N. Feamster, “Web- based attacks to discover and control local iot devices,” in Proceedings of the 2018 Workshop on IoT Security and Privacy, IoT S&P ’18, (New York, NY, USA), p. 29–35, Association for Computing Machinery, 2018.
[12] T.Datta,N.Apthorpe,andN.Feamster,“Adeveloper-friendlylibraryfor smart home iot privacy-preserving traffic obfuscation,” in Proceedings of the 2018 Workshop on IoT Security and Privacy, IoT S&P ’18, (New York, NY, USA), p. 43–48, Association for Computing Machinery, 2018.
The contents of this post were originally written for an essay I had to turn in as part of my assessment for the Internet of Things (IoT) module at Trinity College Dublin.
